Forensic Email Search
In today's arena, most of the users are using email applications for business as well as personal purpose. There are thousands of email applications, with distinct features. As we know, each application has multiple features but some of them having few limitations. Thus, users have to go for third party solution i.e. Email Search Application to analyze the emails. Being developer of data recovery, we have a great understanding of the emails and carving the required information from email header data. It is an advanced email search software, which supports more than 20 email formats and around 750 MIME types. Moreover, it is being used by thousands of forensic professionals and also, refers as a benchmarked email search tool. In addition, the software is equipped with great features such as Forensic email search including Keyword based search, auto tagging, support raw files and so on.
MailXaminer is a tool-kit having multiple functionalities out of which powerful search mechanism is the best feature without any limitation. With this email search software, users can scan, view, search, investigate, analyze, smart review and generate a report of emails in a very less amount of time. In the following section, we will discuss an attractive feature of MailXaminer and also, analyze the header of email forensics.
Advanced Feature of Forensic Email Search Tool
Apart from the bulk of email analysis, the program can execute selective email analysis using advanced search facility. The search feature operates rapidly on a keyword basis. Investigators can analyze emails on the basis of Forensic email search option like advanced search, keyword search, and string search.
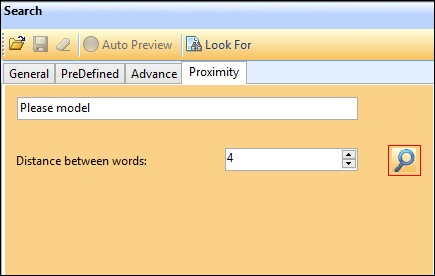
Proximity Search: The proximity search enters two words and ask for providing an approximate number of words between those two characters.
This search may be executed as a hit and trial method that is shown in below snapshot:
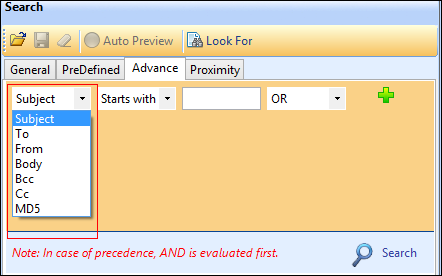
Advance search: As the name defined, advance search option is the most sophisticated and comprehensive search as well for all. This option provides limit a search to emails with particular categories or namespaces. For each search results, it gives the preview in multiple formats. In fact, the search results may be bookmarked or marked with privilege.
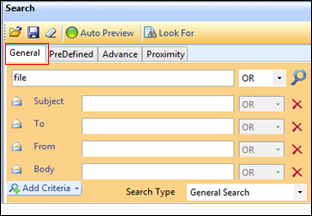
General Search: Basically, the generic search is used for an overall search over the entire or selected email attributes with requires logical operators and any number of criteria used. Users allow to input either a single keyword or a list of keywords and press the search button to get the output. Moreover, fetch results matching with the exact keyword.
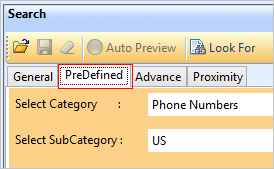
PreDefined search: To perform the PreDefined search on the basis of category or subcategory basis.
Forensics Analysis of Email Search
Despite instant messengers and Social networking sites; emails still having a major carrier of information, used by professional users. The capability of a user to examine and analyze the header of email messages. These header helps to identify any type of manipulation in the database.
Now, let us consider various parameters contained in the email header and their significance in email message authenticity.
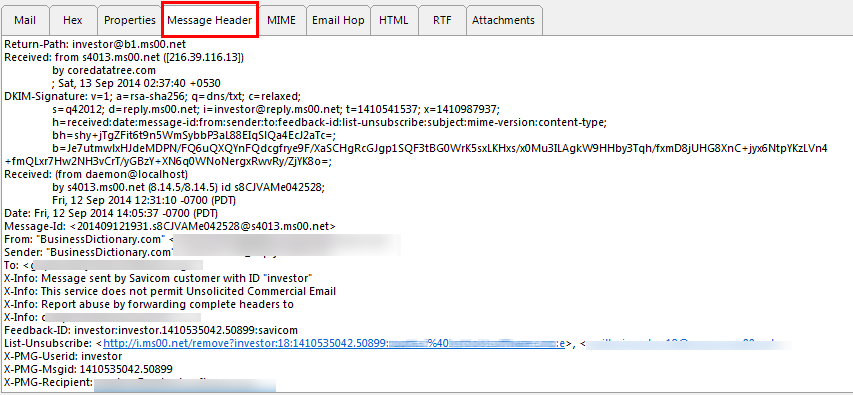
Received: The email header received the message from sender's end, who has to deliver the particular message.
As per forensic point of view, in Email Search Tool the received message has been represented as multiple times. It will show the transaction path from the email message that has been traversed. The received field denotes the transparent details for the particular email. One can easily extract the unique IP address, host name, and other relevant information related to the delivery path of the email message that has traversed.
Return-path: The field of Email Search Software return path header indicates the email address where the notifications for the message should be sent while delivering.
The main purpose of this header to configure the detail through a user itself with the email client and even it may or may not be fully reliable. Forensically, it is necessary to investigate all possible information as it may be helpful to identify the hidden evidence in a simple manner.
DKIM-Signature (Domain Keys Identified Mail): In this field, the signature of an email is saved into DKIM signature header. In Email Search Tool it is a technique to identify the accuracy of any email message to detect email spoofing and spamming.
Forensically, in Email Search Software it signifies that the message is not saved in spambox and the signing authority that is directly responsible for it.
Received From: The received field in email header holds to trace the information for the desired email from where the message has been sent. One can extract the unique IP address, host name, and other information from the delivery path of email
This field able to find out the entire track of information including the IP address of the sender and helps to tell the message received from which ID.
Date: This field handles the date and time when the email message is available for delivery.
As per forensic point of view, this header deals to specify a date during the message was composed and sent to the destination.
From: The email header from field represents the email identity of the sender, who has delivered the email.
Forensically, one can easily come to know the email address of the sender for future purpose. However, many criminals attempt to manipulate the field by using email forging technique. Thus, this field is less reliable or efficient to depend on critical email analysis.
Message-ID: Whenever sending the message, the email message ID is a unique key generated by the server. Every email has a different message identity proof so that it can be identified in a unique manner.
As the unique message id, several spammers attack to manipulate the id. So, the messages id rule can be used to detect any kind of changes done with message id.
X-Message-Info: This field helps to investigate the associated value of all the factors and to receive the information of email message.
X-PMG MSGID: This Pooled Mean Group field means that message comes in a mean group or pool the message identity. Message-ID headers to determine if an email has been forged.
MIME-Version: The MIME-Version indicates the MIME type supported by Forensic investigators.




