Exchange Header Analysis
Nowadays email is the most commonly means of communication for business as well as individual. With a quarter of an average of worker's day spent in reading as well as replying to mails, it is easy to see the importance of mail these days. Unfortunately, email communication is often unprotected to illegitimate utilization due to mainly two essential limitations, i.e. no encryption at the sender end, lack in authentication mechanism. In the following section, we will discuss deep about the Exchange header analysis.
Introduction – Exchange Header Analysis
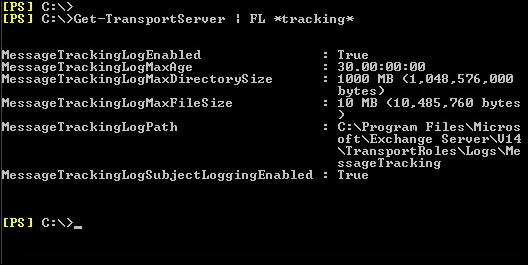
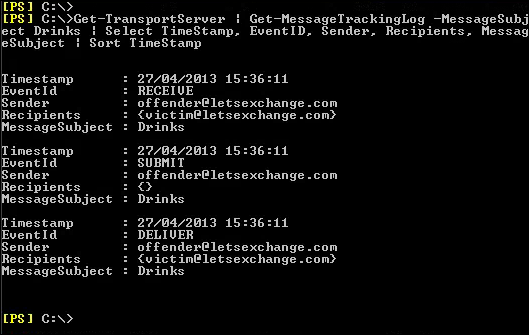
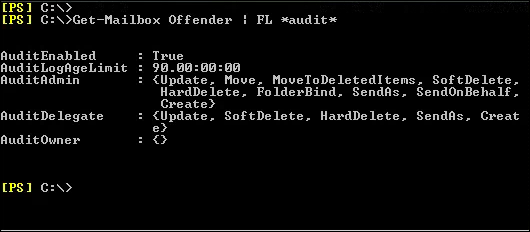
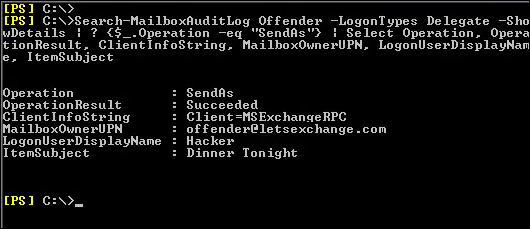
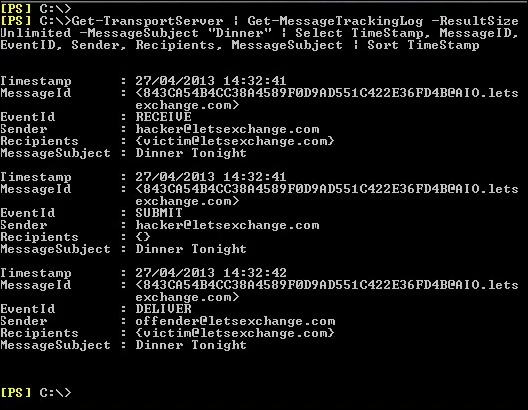
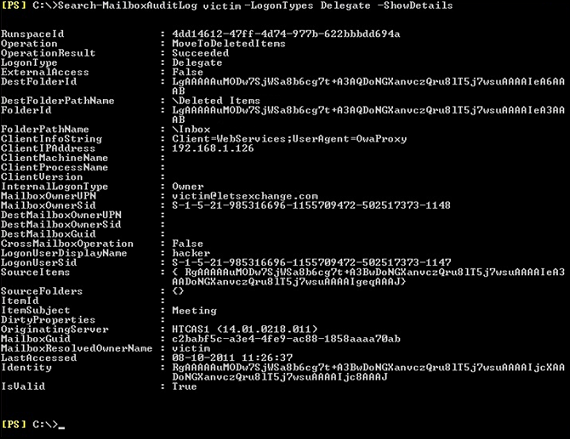
Each Exchange forensic analysis is started on Exchange system itself. If the information that is required does not exist on Exchange, then a deep analysis at the client side is typically performed. For preserving email from a live Exchange server, forensic investigators typically take various approaches that depend on the characteristics of the misuse being investigated. For performing the proper investigation, proper data extraction is required by using Exchange features.
Conclusion
To find an evidence is quiet important for this it is important to perform the Exchange header analysis. The above-discussion covers the same part after understanding user's need and requirements the way for performing analyze of exchange header. Find out any evidence within the emails by advance Email Search Software.