Forensics Analyze of Windows Live Mail Email Header
Despite of an instant messengers and Social networking sites; emails are still having a major carrier of information, used through corporate environments for professional as well as business communication purposes.
The capability of a user to examine and analyze the header of email messages. These header helps to identify any type of manipulation in the database.
When to open the header information for an email, then, the WLM displays the information as:
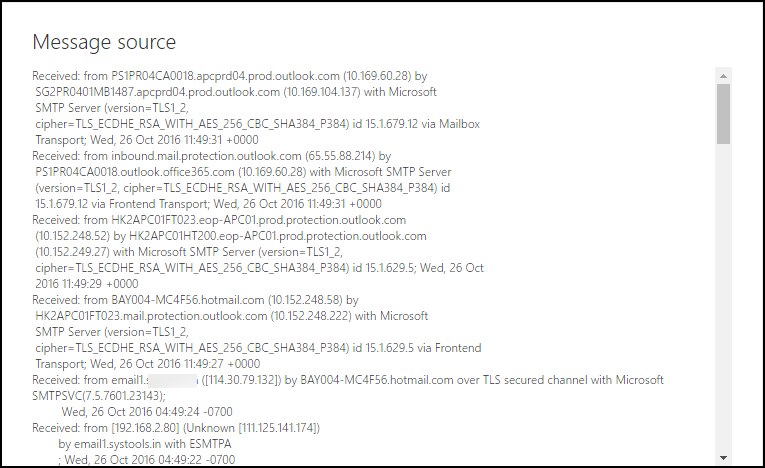
Received: The email header receives the message from sender, who has to deliver the particular message.
As per forensic point of view, in WLM the received message has been represented as multiple times. Investigators might study about these parameters are viewed in WLM. It will show the transaction path from email message that has been traversed.
From: The field of email header represents the name and email address of sender, who has been delivered the message.
Forensically, the email address of the sender will be helpful for future reference. However, multiple cyber crooks attempt to manipulate the filed using email formation approach. Hence, this field is less reliable for critical analysis of an email.
Message-ID: Globally, the identification of message is created uniquely when it is sent/delivered through an individual.
Windows Live Mail header is designed in unique manner. However, doesn't matter first part can be anything but in second the name of machine assigned the particular ID.
Content type: It will help to understand the style of email message which is shown in the application. Multiple types of content denotes the structure of email messages.
As per Forensic investigator, Windows Live Mail is a free Web-based email application to display the type of content. Thus, it can consider a content Type through email header finding the way in which message should be viewed.
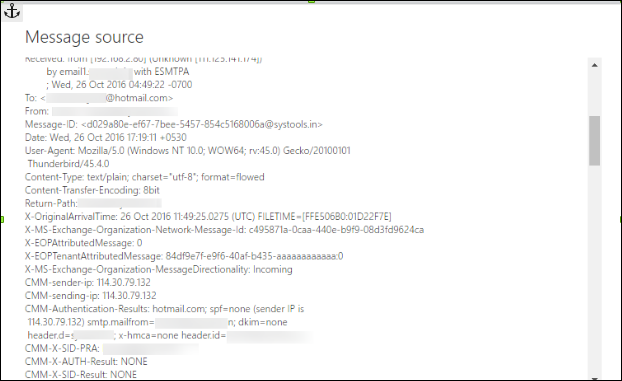
Return-Path: The field of WLM return path header shows the email address where the message notifications should be sent while to deliver the message.
The main purpose of this header to configure the detail through a user itself with the email client and even it may or may not be fully reliable. Forensically, it is necessary to investigate all possible information as it might be helpful to identify the hidden evidence in a simple way.
X-Message-Status: This field helps to see or view the current status or update of the email message.
Forensically, to verify and analyze the status of the email messages. At the end of this field, the accurate status is also up-to-date with time.
X-Message-Delivery: This field assists in receiving the delivery detail of the email message.
Major reason of this header to analyze the delivery information of the email message. It will helpful for users to carry the knowledge of messages.
Content-Transfer-Encoding: During an email message is sent over the network, an encryption is enabled for maintaining the authentication of email. So, content transfer encoding header field specifies the type of encryption which is performed on particular content.
Generally, Windows Live Mail header messages come with 8-bit encryption which is applied on them.
Date: This field holds the date and time when the email message is available for delivery.
As per forensic point of view, this header deals to specify a date during the message was composed and sent. In case, if this header is eliminated through sender's Desktop, it can be added through a mail server or even by some other machine.
X Original Arrival Time: This field helps to inform the original arrival time when a receiver has to receive a specifies message.
In WLM, this message header might reveal the information over Provider ISP forensically.
Authentication Result: This field, tells the authenticated result or output to the receiver at the time of delivered message.
Forensically, in WLM the responsibility of SPF (Server Policy Framework) to check and confirm if the particular Mail Server is authorized for sending email messages to that particular domain. The possible result will show such as 'PASS', 'FAIL' or 'NONE'.
However, in WLM the result will become in 'NONE'
X-SID-PRA & X-AUTH-Result: When this type of field comes in Windows Live mail, in that case, entire mail are switched to a spam folder. Might be the result will become in Fail while receiving this two headers.
X-Message-Info: This field helps to investigate the associated value of all the factors and to receive the information of email message.
DKIM-Signature(Domain Keys Identified Mail): In this field, the signature of an email is saved into DKIM signature header. In Windows Live mail, it is a technique to identify the accuracy of any email message to detect email spoofing and spamming.
Forensically, in WLM DKIM signature uses a simple “tag=NONE”, includes the messages and records of domain signature. If an email is sent through an organization along with DKIM signature that is assigned on the mail, it signifies that the message is not saved in SPAM and the signing authority that is directly responsible for it.
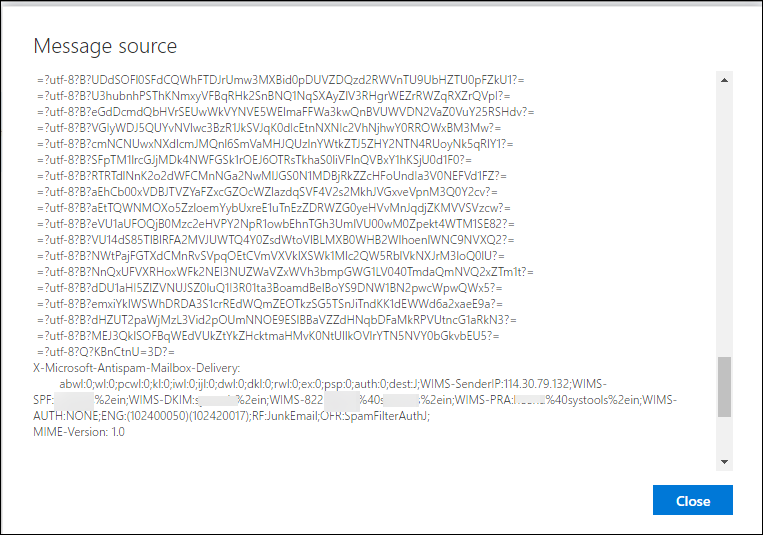
MIME-Version: This MIME version helps to show that the MIME format of email supported by Windows Live Mail.
It signifies, in Windows Live Mail message always contain MIME 1.0 as MIME Version. MIME allows displaying a registration policy which uses Internet Assigned Numbers Authority as a registry for all associated standard and values.